Based on OpenWRT platform, BACRouter could support various VPN, including OpenVPN, wireguard, IPSec, and so on. To reserve maximum storage space for application program, the VPN support is not enabled by default.
Our OpenWRT code is hosted in https://github.com/hvacrcontrol/openwrt, the branch “bacrouter_new” is code for currently production.
The vpn.config in the repository is the configuration with OpenVPN and wireguard enabled.
Precompiled OpenWRT firmware file is: vpn_bacrouter_19.07_8fe8c902.tar.gz
Refer to upgrade-underlayer-firmware-of-bacrouter for how to upgrade the OpenWRT firmware.
Sometime, we need to enable BIP port on the VPN side, the BACRouter firmware from v4.23 intergrated that functionality. Below is a example of how to config it:
Upgrade Openwrt VPN firmware and BACRouter firmware to v4.23
Configure VPN, here is a example of wireguard:
~#uci show network.vpn
network.vpn.proto=’wireguard’
network.vpn.private_key=’####################################’
network.vpn.addresses=’192.168.231.3/24′
~#uci show network.wg0
network.wg0=wireguard_vpn
network.wg0.public_key=’#####################################’
network.wg0.endpoint_host=’###.###.###.###’
network.wg0.endpoint_port=’####’
network.wg0.route_allowed_ips=’1′
network.wg0.persistent_keepalive=’25’
network.wg0.allowed_ips=’192.168.231.0/24′
More info please refer to https://openwrt.org/docs/guide-user/services/vpn/wireguard/start
~#ifconfig vpn
vpn Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet addr:192.168.231.3 P-t-P:192.168.231.3 Mask:255.255.255.0
UP POINTOPOINT RUNNING NOARP MTU:1420 Metric:1
RX packets:557 errors:0 dropped:0 overruns:0 frame:0
TX packets:3593 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:50348 (49.1 KiB) TX bytes:176736 (172.5 KiB)
Add vpn interface to BACRouter:
Original /root/resource.conf:
~#cat /root/resource.conf
{ “eth0”: { “type”: “ETH”, “ifname”: “br-lan” }, “RS485-1”: { “type”: “USB”, “ifname”: “0:0” }, “RS485-2”: { “type”: “USB”, “ifname”: “0:1” } }
Modify /root/resource.conf: (vi is available too)
~#cat >/root/resource.conf
{ “vpn0”: { “type”: “PPP”, “ifname”: “vpn”}, “eth0”: { “type”: “ETH”, “ifname”: “br-lan” }, “RS485-1”: { “type”: “USB”, “ifname”: “0:0” }, “RS485-2”: { “type”: “USB”, “ifname”: “0:1” } }
CTRL+D
Because wireguard works on layer 3 (tun mode), so the type for vpn0 is defined as “PPP”. For VPN works on tap mode, “ETH” should be used.
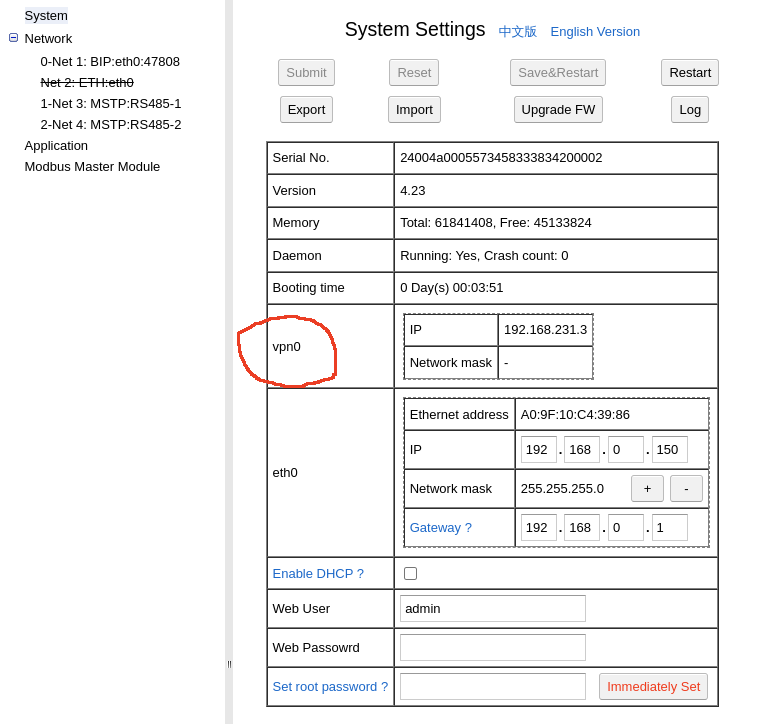
Restart WebUI, the “System Settings” should show as:
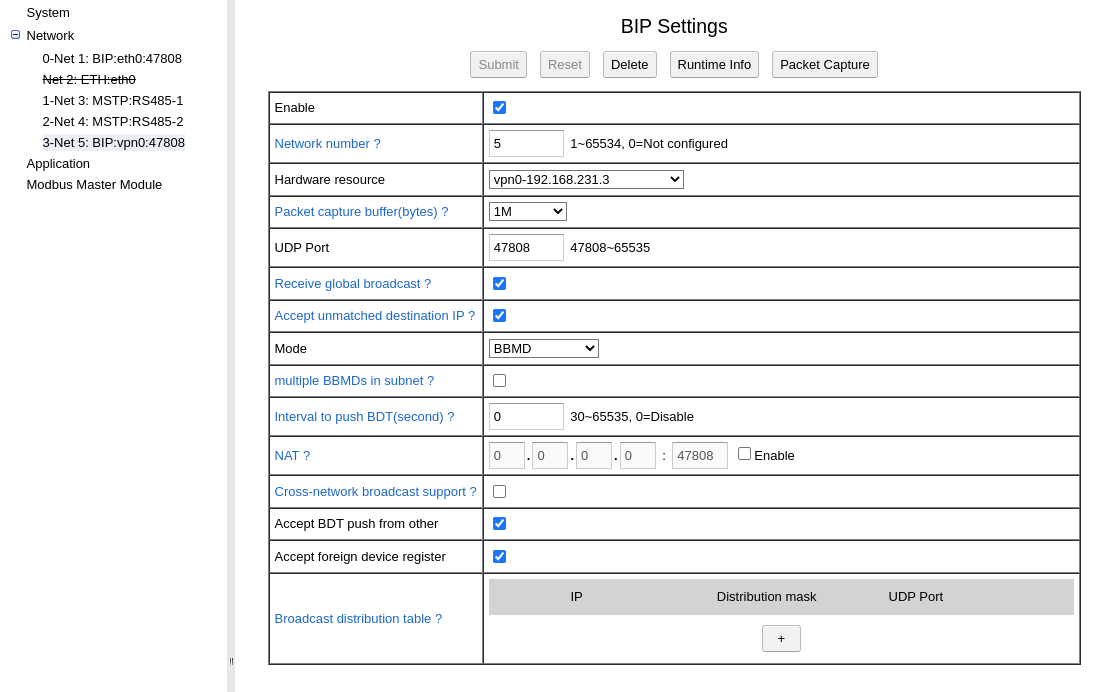
 Create another BIP port on vpn0. Because it’s a PPP interface, only “Foreign Device” and “BBMD” mode is allowed.
Create another BIP port on vpn0. Because it’s a PPP interface, only “Foreign Device” and “BBMD” mode is allowed.
ATTN:When the WebUI and router daemon startup, it will read IP from every interface defined. so only static configured interface works here. For wireguard, no further setting is needed because the ip is statically configured.
For OpenVPN tun mode, please Refer to: assign-static-ip-addresses-for-openvpn-clients When OpenVPN client startups, it may need time to establish connection and get ip from the server. Below startup script will statically pre-configures ip of tun0 to prevent webui’s failing.
~#cat /etc/rc.local
ip tuntap add dev tun0 mode tun
ip link set tun0 up
ip addr add 192.168.231.3/24 dev tun0
/etc/init.d/openvpn start
cd /root
./webui&
exit 0
However, if OpenVPN tap mode is available, tap with bridge is most simple, no adjustment is needed for application level.
Great blog about VPN&BMS: Scott’s Technical Writeups